Reducing the tears: Lessons from the WannaCry cyber attack
- By Eugene Clark
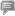 0 Comment(s)
0 Comment(s) Print
Print E-mail China.org.cn, May 26, 2017
E-mail China.org.cn, May 26, 2017
|
|
|
An announcement indicating that there is a disruption to the hospital's information system because of the virus is attached behind a computer monitor at the Dharmais hospital in Jakarta, Indonesia, May 15, 2017. [Photo/Xinhua] |
Looking beyond the headlines, what are some of the lessons learned by this major attack that caused much damage and yet is estimated to have earned the perpetrators a relatively small sum of money? Here's my list:
More attacks will come. First, it is important to realize that this attack is not an aberration. More will be launched and they will become more sophisticated. Health care and education are especially vulnerable to attack and those in charge of security and risk management need to prepare themselves.
Cyber security and managing the risks must be a priority. This means that all those in leadership positions must ensure security is high on the agenda, and that security awareness and preparation are part of every manager's responsibility. This will require training and education. While older managers are well-versed in traditional risks to people and physical property, studies show much less awareness and understanding of risks to digital assets, especially intellectual property. Professionals, such as lawyers and accountants providing services to organizations must also ensure their own security is adequate.
Security is everyone's responsibility. Every employee and stakeholder must also give adequate attention to security at all levels within an organization.
Integrated risk management is required. Security is not an isolated issue. It must be part of an overall strategy for regular risk assessments and information management.
It must include extended security chains and networks. Organizations must focus beyond the four walls of their own activities and encourage and, where possible, require suppliers and customers to also develop adequate security protection.
Get involved with regulatory authorities and standard setting bodies. In addition to working with suppliers and other external members within an organization's network, another vital step is partnering governments, industry associations and bodies such as those that create security and other related standards in order that a workable regulatory and best practice framework is in place and is regularly reviewed.
Mobile devices and the "Internet of Things" make the task harder. In our increasingly mobile world (over 6 billion mobile devices worldwide and over 1 billion in China alone) the context and complexity of security have dramatically changed as these devices increasingly communicate with one another and exchange data. Security can no longer be confined to the four physical walls of an organization. The fact that most employees bring to work their own devices as well as bringing work devices to their home and elsewhere also present new challenges.
The need for speed. One cannot be slack when it comes to security. It is thus important, for example, to implement patches as soon as they become available from product companies. In the case of this particular virus, Microsoft had advocated a patch several months ago and by-and-large, those companies who adopted it were not impacted by this attack.
Have a cyber-attack recovery plan in place. If an attack cannot be prevented, it is important that organizations have a back-up plan, which should be regularly audited/tested to take into account latest developments. Where the attack rises to the level of disaster, organizations must also have communication protocols in place to help limit the damage and ensure an effective recovery.
There are no shortcuts. When it comes to technology and security there are no shortcuts. You get what you pay for, so forget pirated software.
Heed warnings. Organizations should also pay close attention to and heed government warnings on security risks.
Consider cyber insurance. Cyber insurance is becoming part of standard risk management practice for most organizations. As with all forms of insurance, one must read the contract carefully and regularly review the insurance coverage as circumstances change.
Take advantage of existing outside resources. Many governments, institutes and other organizations publish a range of useful security related information and other resources. See for example: GASSP: Generally Accepted System Security Principles, sponsored by the international Information Security Foundation. Find out what resources are available and use them.
Track legal and other regulatory changes. An important component of security and the wider context of information governance relates to legal requirements. Information governance must be an important consideration. Organizations must find the best path through a maze of laws and regulations that impact this area. These include telecommunications laws, corporations law, record keeping requirements, intellectual property protection, privacy, contract law, consumer law, employment law, tort law (e.g. defamation), competition law, criminal law, and others. For those engaged in China, for example, they need to be aware of China's new cybersecurity law going into effect on June 1.
Security is not something that can be left to someone else. Organizations cannot be complacent and think that nothing will happen to them. In this networked world, governments, public and private sector organizations must work together to ensure that risks are identified, security monitored and plans/practices constantly adapted to meet threats hopefully BEFORE they occur.
Eugene Clark is a columnist with China.org.cn. For more information please visit:
http://m.formacion-profesional-a-distancia.com/opinion/eugeneclark.htm
Opinion articles reflect the views of their authors only, not necessarily those of China.org.cn.